In this article, we dive into the complexities and potential pitfalls when implementing ServiceNow´s Vulnerability Response. The transitioning from manual processes to embracing system-supported workflows poses organizational challenges. Let us explore the crucial elements that can make or break your vulnerability management strategy.

Moving from Manual to System-Supported Workflows
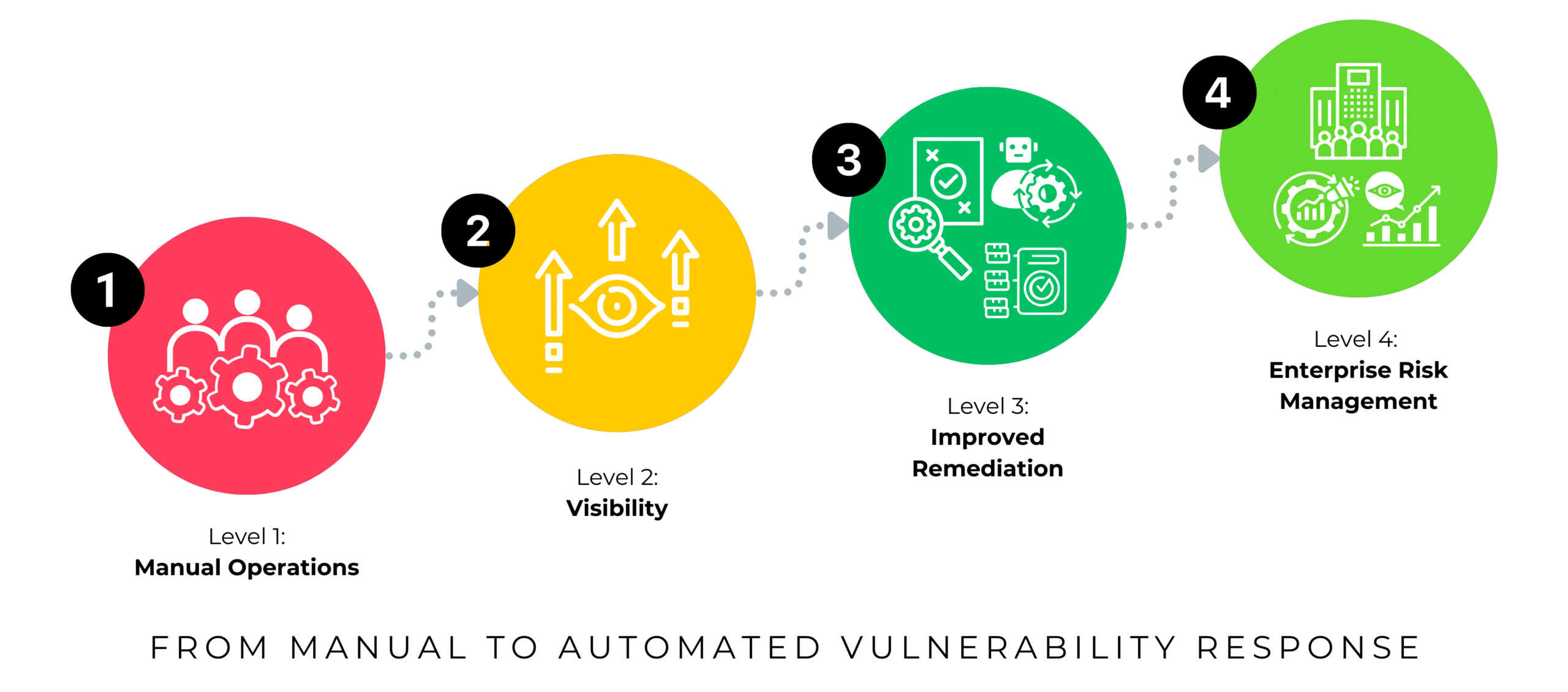
General vulnerability management typically evolves through four distinct levels. At the initial stage, known as “Manual Operations,” organizations grapple with spreadsheets, limited visibility, and frustratingly long response times. This phase is a stark reminder of the inefficiencies that can plague an unoptimized vulnerability management process.
The second level, “Visibility,” represents a significant leap forward. Here, the automation of importing open and fixed vulnerabilities becomes a game-changer. A single system of records is established, enhancing visibility into the organization’s security posture.
The third level, “Improved Remediation“, is where the transformation gains momentum. Key processes such as assignment, prioritization, and grouping are automated. Deferral and risk acceptance processes come into play, alongside comprehensive vulnerability lifecycle management.
The fourth level and zenith of this transformation is the “Enterprise Risk Management” phase. Here, automation reaches its pinnacle with the implementation of Service Level Agreements (SLAs) for remediation targets and Advanced Risk Scoring. Integration with change requests and solutions is also established. The system extends to software exposure assessment, enterprise risk visibility with GRC integration, and mapping vulnerabilities to business services. It’s a holistic approach that takes vulnerability management to the next level.
When climbing the ladder of vulnerability management, there are specific concerns that must be addressed before, during and after implementations of the levels of functionality and the establishment of new workflows.
Strategic Concerns
In the initial workshops focusing on SecOps, including Security Incidents and Vulnerability Response in ServiceNow, the emphasis is on the critical role that maturity plays in implementing robust cybersecurity measures.
A strategic and paced approach to implementation is crucial. We highly discourage rushing into the process and biting off more than one can chew, as it risks heightening organizational resistance to change and endangers the adoption of the tool. Organizations and their personnel must grow and mature alongside the tool. Instantaneous, full-scale implementation is a myth and aiming for that will most likely cause major setbacks.
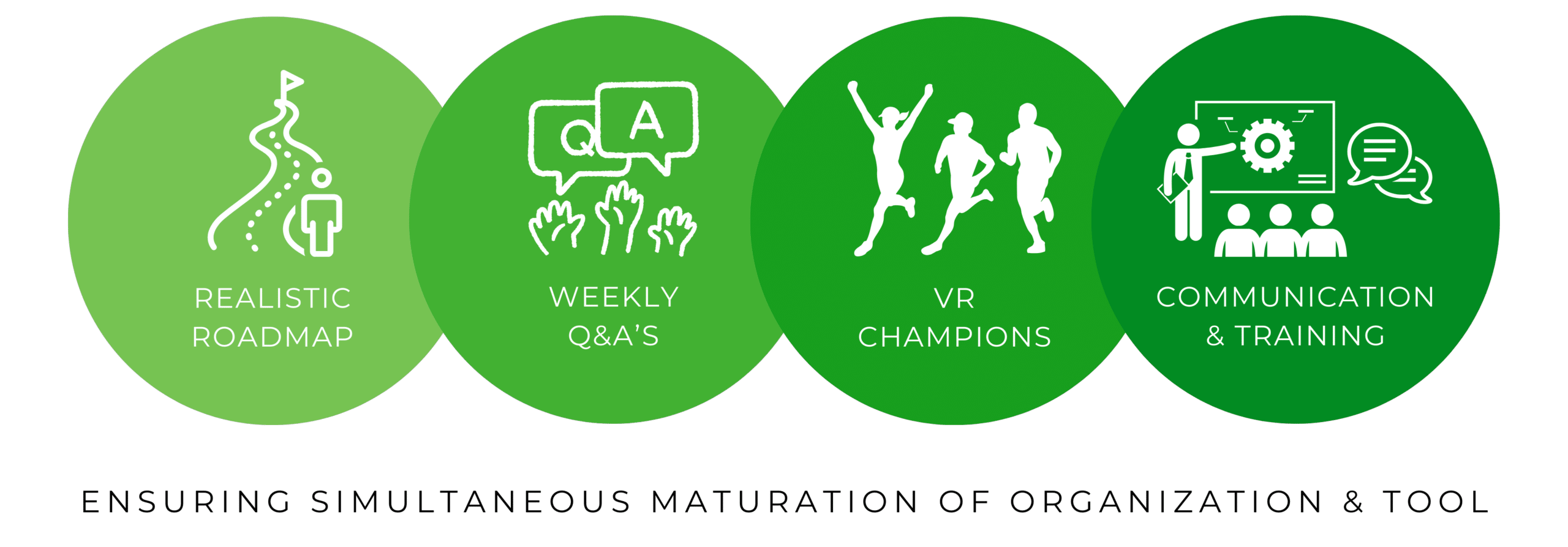
Instead, we recommend a realistic roadmap with the necessary support systems to ensure the complete adoption of Vulnerability Response by IT teams within the organization. Setting realistic goals for the implementation of Vulnerability Response in ServiceNow is not a failure; it’s a prudent approach. Targeting 80% of its full functionality is far preferable to attempting a full-scale rollout right from the start. The IT-teams working with vulnerability response, often work through manual workflows (level 1). Hence, the transitioning to system-supported and automated workflows (level 4) is a big change and is probable to spark some resistance if expectations are not managed and changes are not communicated in the correct manor. What’s essential here, is ensuring that the IT-teams are on board and that both the organization as well as the tool can incrementally mature alongside each other.
Incremental Implementation: A “People-First” Approach
To ensure maximum adoption and utilization of Vulnerability Response in ServiceNow, we recommend an incremental approach to implementation. The functionality of Vulnerability Response in ServiceNow is extensive, and the tool must mature in collaboration with the people utilizing it.
The roadmap we advocate is founded on a “people-first” mentality. It involves alignment among the ServiceNow-product owner, management, and Vulnerability Admins regarding expectations and the scope of implementation. This collaborative effort lays the foundation for as seamless a transition as possible.
In our opinion, the communication must not only focus on the ‘why’ and the ‘how’. When people become resistant to change in any scenario, you cannot only focus on rationalizing why and how the change is necessary and beneficial – one must also take feelings and concerns into account while always taking care of the people who are affected by change. This means communicating the objectives and process clearly, while always communicating that you are available in listening to, and addressing concerns that might arise.
By focusing heavily on the training of staff and stakeholders and the adoption of Vulnerability Response in ServiceNow, one ensures that the ability to formulate requirements matures within the organization – making further development of the tool easier at a later point.
Weekly Q&A’s
To ensure that the Vulnerability Admins and Analysts are fully on board and able to champion the solution to the rest of the IT-department, we recommend weekly Q&A’s with our experts. In our experience, this helps a lot when it comes to adopting Vulnerability Response – it is important that the SecOps-department can raise their level of knowledge surrounding both SecOps, Vulnerability Response as well as the shift from manual to system-supported workflows. If they are not competent in handling the Vulnerability Response software, the IT-teams that they report their findings to, will be stuck on an island without the proper guidance needed to remedy the vulnerabilities within their given areas of responsibility. Training and educational workshops must run parallel to the implementation process – a critical aspect often overlooked.
During the initial phases of an implementation, the weekly Q&A’s, training sessions and educational workshops are planned out for the entire project, ensuring that any organizational challenges can be considered and resolved. This approach also ensures that the Vulnerability-admins, -analysts and the IT-teams in the organization can take ownership of the implementation-project, as well as championing the tool going forward.
VR Champions
We always recommend appointing Vulnerability Response (VR) Champions within the organization – ideally, one for every IT-team that is in touch with the tool. This can be a real game-changer. VR Champions drive awareness and adoption while acting as advocates for the tool within their respective departments. These champions will also help when you want the tool to evolve further at a later point, as they gain a deep understanding of the tool as well as the organization surrounding it.
Conclusion
In conclusion, Vulnerability Response in ServiceNow is a crucial component of modern cybersecurity. The constantly evolving threat landscape requires organizations to have robust systems and workflows in place to identify and address vulnerabilities promptly. When implementing Vulnerability Response in ServiceNow, a strategic and incremental approach, along with proper change management, ensures the successful adoption of this essential tool, safeguarding your organization against cyber threats.